Secure
Electronic Storage System for Certified Original
Masahiro Yamaguchi
Associate Professor,
Imaging Science and Engineering Laboratory
Tokyo Institute of Technology
Table of Contents
1. Introduction
2.
Concept of the Secure Electronic Storage System
3. The developed Prototype
4. Implementations
and Applications
5. Future Task
6. Conclusion
Since 1998/12/8 by Masahiro Yamaguchi
Back
to Ohyama/Yamaguchi Homepage
1. Introduction
The utilization of information systems is proceeding rapidly in various
fields such as electronic commerce, healthcare, etc., and the storage of
the documents whose preservation is mandated by statute is impressing heavy
burden on enterprises. Therefore, the realization of the electronic preservation
of documents is strongly expected for the efficient business as well as
for the reduction of storage costs.
The "Advanced Information and Communication Society Promotion Headquarters"
and the "Working Party for Review of Institutions and Systems" established
by the Cabinet studied these matters from the aspect of decreasing the
social cost and the improving the efficiencies of administrative processing.
A conclusion of their investigation is to recognize the electronic preservation
of documents in principle. It also points out that it is compulsory to
secure the data genuineness, readability and preservability.
The "Secure Electronic Storage System for Certified Original" or "Electronic
Safety Box" was proposed under above background, to enable the electronic
preservation of documents and to promote paperless way to deal with the
accounting ledgers, tax recordings, applications, reports, etc. The project
to develop the "Secure Electronic Storage System for Certified Original"
is carried out in FY 1997 by the New Media Development Association conducted
under the Advanced Software Enrichment Project of Information-technology
Promotion Agency, Japan(IPA). In this paper, the concept of the "Secure
Electronic Storage System for Certified Original" and the overview of the
developed system are given.
Back to TOP
2. Concept
of the "Secure Electronic Storage System for Certified Original"
(1) Requirements for the Electronic Storage
According to the report issued by the Working Party for Review of Institutions
and Systems, securing the genuineness, readability and preservability of
data are necessary to allow the electronic storage of documents to be requiring
preservation, and the enhancement of the probative value as an evidence
is also required. In general, data genuineness, readability and preservability
are secured by appropriately combining technological, institutional, systematic
measures.
Although all types of hazards are covered by the aforementioned countermeasures
in the conventional system of document preservation in the form of papers
or films, new hazards arise when engaging in electronic preservation. Appropriate
measures must be devised to certify that the stored information is the
original and has not been altered.
In the electronic notary system, the stored data are certified to be
unaltered by a trusted third party, namely, the requirements for electronic
preservation are satisfied by devising the institutional and systematic
measures. Meanwhile, by developing new electronic storage system having
the functions equivalent to the papers or films, it is also possible to
devise the technical measures with respect to new hazards which arise when
engaging in electronic preservation. In this case, there will be no need
to change conventional document management systems or to establish new
regulations and monitoring system. Therefore, it is comparatively easy
to implement the electronic storage of the documents requiring the preservation.
The Secure Electronic Storage System for Certified Original has been
developed with the aim of satisfying aforementioned technical requirements
by incorporating a mechanism to physically and logically maintain the security
of stored information.
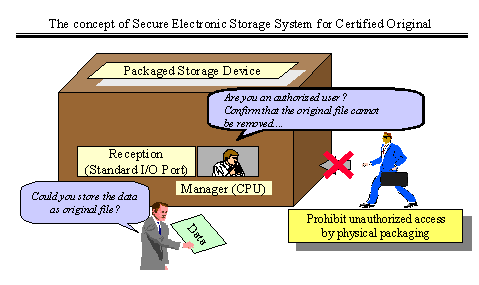
(2) Method of Protecting the Original
In the Secure Electronic Storage System for Certified Original, the stored
information is secured by physical and logical protection against unauthorized
access. The methods for protection are summarized hereunder (See fig.1);
-
1) All access to the memory (ex. Read/Write) is controlled by the central
processing unit (CPU).
-
2) Access to the storage device is restricted to only the standard input/output
(I/O) port.
-
3) The storage device is packaged to inhibit component replacement or data
alteration.
-
4) The control program is stored in a ROM unit to render tampering impossible.
Above functions are equivalent to those of a smart IC card, which is coming
into wide use recently, and the data stored in the system is only accessed
by a method prescribed by the control program. This control program prohibits
the alteration of stored original data, so that the following functions
are realized;
-
Since the access to the system is restricted through the standard I/O port,
the readability is achieved regardless of the type of storage medium.
-
The erasure and the alteration of data stored as the original are prevented.
Whenever an unauthorized entry is attempted by breaking the package physically,
the trace of unauthorized access is recorded. (tamper-resistance or tamper-evidence)
By implementing these functions, it becomes possible to secure the genuineness,
readability and preservability that are almost equivalent to the conventional
system using papers. Also, the access logs are recorded to improve the
probative value of the stored data.
Considering the practical use of the system, this system can be used
to store the data files other than the original. Accordingly, four kinds
of information status are defined; provisional original, authorized original,
authorized copy and not specified, as described in section (4). By controlling
the access rights to the stored files based on the status, the distinction
of the original and copy becomes possible. This file status management
is basically the same as the method adopted by the Common Standard for
Electronic Storage of Medical Image Files published by Medical Information
System Development Center (MEDIS-DC).
Back to TOP
3. The developed prototype
(1) Outline
The developed system consists of the storage device and the host computer.
The storage device is available in the forms of both unitized systems such
as hard disks and removable systems, for example, CD-R and magneto-optical
disks (MOD). Although the method for the physical and logical packaging
depends on the unitized type and the removable type (see section 2), the
host computer recognizes them as identical devices except for the memory
size.
A versatile type PC is used as the host system, which manage the user
request and process the I/O to the storage device. In this system, the
interface between the storage device and host computer (standard I/O port
specifications) is designed with rigid specifications, though the standardization
is required, and can therefore be utilized by not only the PC used in the
prototype but also any type of host computers.
(2) Packaging
The storage device is packaged and tamper-resistant, so as to protect against
unauthorized physical access; direct access into the memory and any change
of the control program. The communications between the storage device and
host computer is limited to only the I/O port as described in section (3).
To use a removable storage medium such as an optical disk, logical packaging,
that is the each medium is individually managed by giving the identification
(ID) number and the message authentication is attached to the stored data.
The ID number and the message authentication code (MAC) are kept in the
local memory of the storage device, and are protected against unauthorized
use and alteration. Namely, the data in the removable medium is attributed
to corresponding storage device, and any change of data by the other system
is detected by the verification of the ID number and MAC. Although logical
packaging is realized by this kind of approach, the complete prevention
of the erasure or the alteration is not possible if conventional versatile
media are used, and it should be noted that the slight reduction of security
level is difficult to be avoided if compared with the unitized-type storage
device.
Incidentally, the current prototype can use the MOD conforming to the
common standard for medical image storage as well as CD-R as the removable
medium, despite that the storage system can be realized independent on
the type of the storage media. If using the common standard MOD, unauthorized
access is extremely difficult, because it has the security mechanism that
prevents the access with an ordinary MOD drive.
(3) Data Input/Output
The contents of stored data are read by displaying them on the monitor
of the host computer or making a hard copy by the printer. To secure the
readability of the stored original data, it is necessary to guarantee that
the same results would be obtained even if the data are displayed by various
different host systems. For this purpose, the specification of the data
I/O port is strictly defined, while the lower layer protocol are not so
that it is possible to select an existing communication interface in conformance
with the type of the hardware, such as TCP/IP, SCSI, and RS232C.
In the communication between the host computer and the storage device,
a "command" conforming to the required operation is transmitted to the
storage system. All the functions of the storage system are defined by
the commands, such as "create file," "read data" and "write data." The
results are displayed as "response" from the storage system, and whenever
a undefined or non-permitted command was received, an "error" response
is returned.
(4) File status control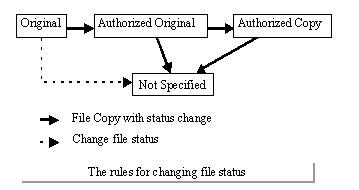
As described before, since files other than the original data are also
stored in this system, following four types of file status are defined
to control the file access, for the purpose to discriminate the original
and others and to guarantee the uniqueness of the original information:
-
1) Provisional Original
-
This type of status is given to the files which have the possibility of
the preservation to be required. This type of file can be deleted, but
alterations other than the additions are prohibited.
-
2) Authorized Original
-
Files whose preservation is mandated by statute have this type of status.
Alteration other than additions, also erasure, are prohibited.
-
3) Authorized Copy
-
This expresses that the file is an attested copy of the authorized original.
Any access except for readout is prohibited to prevent the tampering.
-
4) Not Specified
-
Not Specified type is given to the files which are not given access control.
All kinds of access such as read, write, erasure and others are permitted.
The change of file status is limited to the directions indicated in Fig.2,
so that it is impossible to alter an original file or replace an Authorized
Original with a Not Specified file. Also, the transcript can be produced
from the original file, and the original can be distinguished from the
copies as well.
In addition, the authorized original is produced only from the provisional
original, so as to keep the confidence of the original file, by limiting
the generation of the original file to specific persons or systems having
the right to generate the provisional original files. For example, regarding
the electronic storage of medical images, only the images originated by
the authorized imaging apparatus have the status of provisional original.
Although rewriting the original file is prohibited as a means to prevent
original file tampering, there may be a need to make additions or revisions
to the original files. Therefore, this system provide a function to enable
appending new data into authorized or provisional original files. In this
case, appended date/time and history are saved as well as all the appended
data, and the probative value of stored data is still retained. It should
be noted that the management of appended data, such as specifying the edited
part of data, are to be done by an application program.
(5) Recording Access Log
The access log to the storage device is recorded, to enhance the probative
value of stored data. The access date/time and the access type such as
write, append or change of file status, are automatically recorded in the
storage device. When several persons use the storage system, the log includes
the information that identifies the individual who accessed to the system.
A timer built into the storage system is used to specify the date/time
of access.
Moreover, the history of the system administration (see section (9)),
such as the registration of users and timer setting is also recorded. Accordingly,
even if the administrator's rights were fraudulently used and an attempt
made, for example, to change the timer setting to tamper with past data,
the traces of the attempt is recorded. Furthermore the recorded log information
cannot be removed even by the administrator, as with the authorized original
file. Incidentally, the recording of access log is conceived to be effective
for suppressing fraudulent actions.
(6) User Identification
When this system is connected to the network and employed by several users,
the function to identify the individual user can be utilized so as to make
the system administration easier. The key information of each user is securely
registered in the storage device, and the user is identified by the authentication
between the smart IC card possessed by each user and the storage device.
Using this identification, the access control depending on each user and
the recording of the user identification to the log become possible.
(7) Copy and Move of Original File
To certify the original data even when the original data is copied or moved
between the storage devices through a network, the functions of "Copy"
and "Move" of original file are incorporated in this system. The copy created
in another device has the authorized copy status. When an original file
is moved to another storage device, the data in the source storage device
is removed and the new file in the destination becomes the original. To
guarantee that these functions are only performed between the valid storage
devices, the validity of the storage systems are confirmed by the mutual
authentication. The data integrity during the copy or move is also assured
by message authentication.
(8) Backup of Original File
Though the preservability of the stored data depends on the performance
of each recording medium used in the storage device. In the system developed
this time, the automatic backup function is implemented to increase the
data preservability. As the method of securing the data preservability
is realized through internal processing and does not affect the external
interface, arbitrary method can be applied. In the developed prototype,
the original data can be recovered from the backup data, which is automatically
generated in the storage device, even from the damage that cannot be corrected
by the error recovery function of the recording medium.
(9) Administration of Storage Device
The administration of the storage device such as the user registration
or timer setting can be performed only by an authorized administrator.
After the verification of authorized administrator using a smart IC card,
the administrative functions become effective. The history of the administrative
operation is also recorded in a log, which cannot be removed or altered
even by the administrator.
(10) Data Format
Standard data format is necessary to keep the readability of the stored
information. Standardization is a future task, and we assume following
two types of data formats.
-
a) Common Format suitable for accounting
-
The data format enabling the reproduction of the style of ledgers, invoice,
and other accounting forms is defined as "Common Format." The image of
the forms including ruled lines can be easily reconstructed from the data
described by tagged text format.
- b) Common Standard for Electronic Storage of Medical Image Files
-
The data format and the MOD defined in the Common Standard published by
MEDIS-DC is used for the storage of medical images, so as to keep the consistency
with the existing systems for medical image storage.
-
Back to TOP
4. Implementations
and Applications
The implementation of this system has large variations, from compact, handy
and portable system to a large-capacity file server, because only the specification
of the I/O interface have to be designated and the type and capacity of
memory or CPU are not restricted. Arbitrary type of recording medium can
be used, moreover, and it will be possible to utilize this system as a
versatile-type secure electronic storage system.
For example, this system can be used as a peripheral of host computer
system just like a printer, which is conventionally used for the output
of documents to be preserved. It is easy to replace the conventional method
of document output with a printer by that using the electronic storage
system, resulting in the efficiency being improved in the retrieval and
reuse of the stored data, as well as space savings. It is also possible
to use this system with LAN or Intranet, and the storage device is directly
connected to the network and the users having access to the network can
use the device. Specifically, by utilizing a software for electronic signature
or seal ("inkan" in Japanese) and the function of this system for appending
data into the original file, one can impress an electronic seal on an original
document generated by oneself or another user through the network.
5. Future Task
* Standardization of I/O command and communication protocol
* Management of users and other storage devices through network including
authentication keys.
* Electronic signatures or electronic seal (inkan).
* File retrieval for the reutilization of stored data.
* The certification of dispatch and arrival of messages such as e-mail.
* Adapt to a secure file-server, on-line application system, encription
key storage, etc.
Back to TOP
6. Conclusion
The system developed in this project alleviates the requirements to the
systematic countermeasures against the hazards that appear in the digital
storage of original documents, by employing technical countermeasures such
as the protection against tampering. Therefore the introduction of the
electronic storage is relatively easy without establishing social system
for administration. This system will likewise beneficial for the electronic
data storage in Electronic Notary Centers and Certificate Authorities.
Studies are currently given to the use of WORM (write one read many)
storage media such as CD-R for this kind of applications, but it should
be noted that even WORM does not guarantee the prevention against alteration.
On the other hand, the Secure Electronic Storage System for Certified Original
certifies the original documents regardless of the type of storage medium,
by the physical and logical tamper-resistant or tamper-evident mechanisms.
Therefore each user can flexibly select optimal type of storage medium
suitable for one's application field considering the technological level
and the cost-performance. Furthermore, this system has the advantage at
the point that the system is capable of coping with future technical innovation.
Back to TOP
If you have comments or suggestions, email me at



